IT security teams face a constant battle to keep on top of the security controls provided by their core suppliers. They are required to show how a move to this platform, operating system or cloud will enhance their organisation’s security, and why.
The Security Stack Mappings for Azure research project from Microsoft and MITRE-Engenuity is designed to help improve the information available for IT security teams.
What is the Security Stack Mappings for Azure research project?
The Security Stack Mappings research project is devised by MITRE-Engenuity, the organisation behind the MITRE ATT&CK framework. ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge, and the framework is a comprehensive record of the different techniques used by cyber attackers.
The MITRE ATT&CK framework is used by threat hunters, red teamers, and defenders to assess an organisation’s risk against the threats they may face.
The Security Stack Mappings for Azure research project aims to improve the data available for organisations which explains how a platform’s in-built security controls support them against the specific adversary tactics, techniques, and procedures (TTPs) that they are working to protect their organisations against.
Put simply, the Security Stack Mappings for Azure research project has mapped 48 security controls contained in the Microsoft Azure cloud platform against one or more of the threat techniques listed in the MITRE ATT&CK framework.
The project has created a library of mappings that provides detailed information about the protection provided by these controls against the TTPs that organisations may face.
How the security controls were mapped
In order to carry out the mapping exercise, the Center for Threat-Informed Defense (CTID) run by MITRE-Engenuity worked with Microsoft Azure to create a fresh methodology that would reach their desired outcomes. The five step methodology included:
Step 1: Identify platform security controls – identify the set of security controls available on Azure for analysis.
Step 2: Security control review – review each security control’s documentation, and identify the set of ATT&CK (sub-)techniques that it mitigates.
Step 3: Identify mappable ATT&CK (sub-)techniques – use the information gathered above to map the security control against the set of ATT&CK (sub-)techniques it mitigates.
Step 4: Produce score assessments – security controls were assessed against the scoring criteria. The scoring rubric took into account three key areas:
- Function – is the security control intended to protect, detect, or respond to an adversary behaviour.
- Effectiveness – each security control’s effectiveness was scored against criteria for its function, and rated as minimal, partial, or significant.
- Additional factors – coverage, temporal (real-time, periodic, or externally triggered), and accuracy.
Step 5: Create mapping files – every mapped control is placed in a mapping file which records all the data gathered throughout the project.
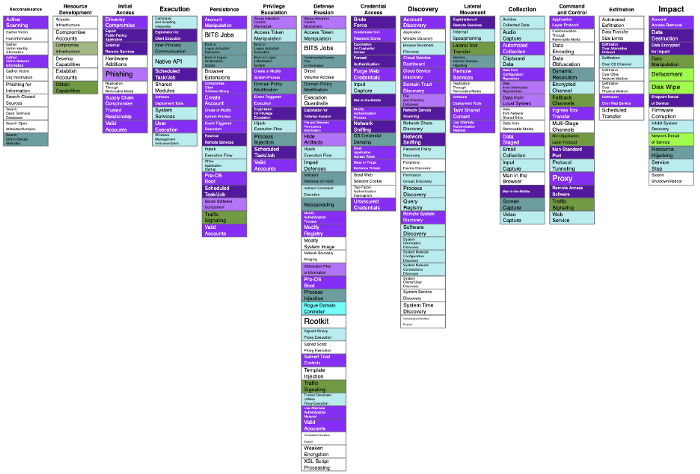
Overview of the Security Stack Mappings for Azure research project coverage
Why is the Security Stack Mappings for Azure research project valuable?
Microsoft Azure contains a suite of built-in security controls. However, it can be challenging for their customers to understand how these security controls support their information security requirements.
The mappings project gives them detailed information about how these in-built security controls mitigate against the MITRE ATT&CK framework, a familiar framework that many IT security professionals already use to identify their threat profile. They can then use this information to make informed judgements on their readiness against today’s threats.
Where Microsoft Azure is the first product to have carried out this exercise, many more will be released soon. The CITD is already working on Security Stack Mappings with AWS, Windows, and MacOS, and other leading providers are sure to follow.
For organisations everywhere, this is a great initiative that will support security and risk management teams to balance the risks between digital transformation, effective work practices, and information and network security
Stay safe.







