Pa$$W0rD123: Why secure passwords alone aren’t enough to protect your network security
Almost every account we use on a day to day basis is…
As an online gaming company, you handle large sums of customers’ funds and personally identifiable information (PII), making you an attractive target for cyber attackers, who use increasingly sophisticated ways to target and compromise your business. This risk of adversarial actions and the accountability placed on you by regulatory frameworks to protect customers’ personal data have created heavy data protection obligations, strengthening the need for effective cybersecurity practices.
Data breaches, fraud attempts, DDoS attacks, regulators’ fines, and more will damage your reputation, cause business disruption, cost you money, and could even cause you to suspend your operation. It’s never too soon to take action to improve your company’s cybersecurity resilience and protect your customers’ funds and data.
We help our clients to see the big picture, securing companies rather than just networks, implementing agile cybersecurity consulting practices focused on People-Processes-Technologies in a close alignment with our clients’ business needs.
At Cynance, we understand how the gaming industry operates, and have gained the experience to support your business whether you are a licensee, operator, platform provider, games developer, or any other online gaming related business with our cybersecurity and data protection services.
Our team worked with gaming companies of all shapes and sizes, successfully consulting to some of the industry’s most prominent players and gaming startups alike. As your information security partners, we help you protect your players, platforms, and products, and provide you with comprehensive security documentation, including detailed assessment reports, internal policies, and guidelines documents to enhance your company’s security posture and demonstrate your information security good practices to clients and regulators..
Our flexible pricing structure, highly personalised service, and ability to get things done with little interruption to your day to day business, make us the ideal partners to help you stay safe, prepare for and pass external audits, and comply with industry standards, regulations and best practices, such as gambling authorities’ regulations, GDPR, ISO 27001, and more.
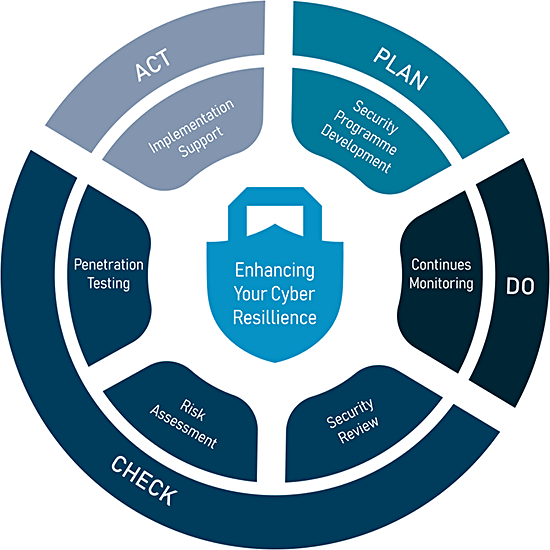
Thoroughly evaluate the security posture of your applications and platforms with simulated real-life hacking tactics.
Analyse your IT architecture and core infrastructure components, identify weaknesses and areas of potential threat.
Receive guidance and support through the journey of information security standards certification.
Protect the personal data you process; demonstrate accountability by creating a comprehensive data protection framework, supported by appropriate internal procedures.
Assess your company's compliance with the industry regulation's information security requirements, and develop strategies to achieve compliance.
Almost every account we use on a day to day basis is…
Stolen health data is extremely lucrative on the black market, and private…
Your startup is up and running, but how secure are you? Begin…
Malicious actors use various techniques in order to obtain information from unsuspecting…
OSINT refers to information that can be freely and legally gathered from…
What you need to know about meeting GDPR information security requirements and…
You care about your information security, so do we. We support you and your team to enhance your organisation’s information security posture to a level that is appropriate for you at any given time. At Cynance we breathe, eat, and sleep cybersecurity, applying our experience and knowledge to solve even the most complex security problems. Contact us now and take a step to improve your information security.
| Cookie | Duration | Description |
|---|---|---|
| _GRECAPTCHA | 5 months 27 days | This cookie is set by Google. In addition to certain standard Google cookies, reCAPTCHA sets a necessary cookie (_GRECAPTCHA) when executed for the purpose of providing its risk analysis. |
| cookielawinfo-checkbox-advertisement | 1 year | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Advertisement". |
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| elementor | never | This cookie is used by the website's WordPress theme. It allows the website owner to implement or change the website's content in real-time. |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
| Cookie | Duration | Description |
|---|---|---|
| _ga | 2 years | This cookie is installed by Google Analytics. The cookie is used to calculate visitor, session, campaign data and keep track of site usage for the site's analytics report. The cookies store information anonymously and assign a randomly generated number to identify unique visitors. |
| _gat_UA-176747747-1 | 1 minute | This is a pattern type cookie set by Google Analytics, where the pattern element on the name contains the unique identity number of the account or website it relates to. It appears to be a variation of the _gat cookie which is used to limit the amount of data recorded by Google on high traffic volume websites. |
| _gid | 1 day | This cookie is installed by Google Analytics. The cookie is used to store information of how visitors use a website and helps in creating an analytics report of how the website is doing. The data collected including the number visitors, the source where they have come from, and the pages visted in an anonymous form. |
| CONSENT | 16 years 5 months | These cookies are set via embedded youtube-videos. They register anonymous statistical data on for example how many times the video is displayed and what settings are used for playback.No sensitive data is collected unless you log in to your google account, in that case your choices are linked with your account, for example if you click “like” on a video. |
| Cookie | Duration | Description |
|---|---|---|
| IDE | 1 year 24 days | Used by Google DoubleClick and stores information about how the user uses the website and any other advertisement before visiting the website. This is used to present users with ads that are relevant to them according to the user profile. |
| test_cookie | 15 minutes | This cookie is set by doubleclick.net. The purpose of the cookie is to determine if the user's browser supports cookies. |
| VISITOR_INFO1_LIVE | 5 months 27 days | This cookie is set by Youtube. Used to track the information of the embedded YouTube videos on a website. |
| YSC | session | This cookies is set by Youtube and is used to track the views of embedded videos. |